PluralSight – Blue Team Tools Path
English | Tutorial | Size: 1.68 GB
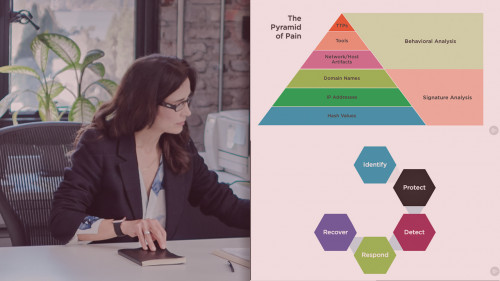
MITRE ATT&CK® is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community. With the addition of MITRE Shield, you now have a 360 degree view of attack scenarios and the data and capabilities needed to stop them.
Further details on the MITRE Shield framework
Further details on the MITRE ATT&CK® framework
Our blue team tooling courses focus on the use of a specific industry-standard, open source tool to protect, detect, and respond against targeted threat actor techniques in an enterprise environment. Knowing what a tool is and how it can be integrated into your overall enterprise security strategy will ultimately lend to your ability as an organization or an individual to defend against specific adversary activity.
Courses in this path
Introduction
The first course in this series discusses the use of open source, blue team tools to fill the gaps in your enterprise security, in turn, enable your information security organization to evolve their capabilities as fast as the threat actors you are defending against.
Blue Team Tools: Defense against Adversary Activity Using MITRE Techniques by Aaron Rosenmund 19m Duration (23)
Network Analysis
In this section, you will learn about the tools associated with network analysis to detect related data source TTPs and actively meet the adversary’s activity with a response before you encounter it.
Network Analysis with Arkime by Josh Stroschein 45m Duration
Network Analysis with pfSense by Joe Abraham 38m Duration
OS Analysis
In this section, you will learn about the tools associated with OS analysis to detect related data source TTPs and actively meet the adversary’s activity with a response before you encounter it.
OS Analysis with HELK by Aaron Rosenmund 29m Duration
OS Analysis with RegRipper by Shoaib Arshad 39m Duration
OS Analysis with Wazuh 4 by Zach Roof 37m Duration
OS Analysis with Volatility by Tim Coakley 27m Duration
OS Analysis with The Sleuth Kit & Autopsy by Ashley Pearson 15m Duration
OS Analysis with osquery by Joe Abraham 31m Duration
OS Analysis with OSSEC 3 by Michael Edie 24m Duration
OS Analysis with Nagios by Owen Dubiel 22m Duration
Infrastructure Analysis
In this section, you will learn about the tools associated with infrastructure analysis to detect related data source TTPs and actively meet the adversary’s activity with a response before you encounter it.
Cloud Infrastructure Analysis with Scout Suite by Guillaume Ross 29m Duration
Cloud Infrastructure Analysis with Prowler by Tim Coakley 24m Duration
Container Infrastructure Analysis with kube-hunter by Zach Roof 42m Duration
Container Infrastructure Analysis with Trivy by Zach Roof 49m Duration
File Analysis
In this section, you will learn about the tools associated with file analysis to detect related data source TTPs and actively meet the adversary’s activity with a response before you encounter it.
File Analysis with TruffleHog by Tim Coakley 23m Duration
Application Analysis
In this section, you will learn about the tools associated with application analysis to detect related data source TTPs and actively meet the adversary’s activity with a response before you encounter it.
Application Analysis with Endlessh 1 by Laurentiu Raducu 16m Duration
Application Analysis with ModSecurity by Michael Edie 24m Duration
Application Analysis with SonarQube by George Smith 34m Duration
Incident Management
In this section, you will learn about the tools associated with incident management to detect related data source TTPs and actively meet the adversary’s activity with a response before you encounter it.
Incident Management with TheHive by Nick Mitropoulos 27m Duration
Threat Intelligence
In this section, you will learn about the tools associated with threat intelligence to detect related data source TTPs and actively meet the adversary’s activity with a response before you encounter it.
Threat Intelligence with MSTICPy by Ian Hellen 33m Duration
Threat Intelligence with MISP by Phil Chapman 21m Duration
Number of Courses 22 courses
Duration11 hours

RAPIDGATOR
rapidgator.net/file/c9653813970351454094740f82948a10/Pluralsight_-_Blue_Team_Tools_Path.part1.rar.html
rapidgator.net/file/19819a874fec7b349acce6032b91aabe/Pluralsight_-_Blue_Team_Tools_Path.part2.rar.html
rapidgator.net/file/f53b0e5813de875ba59b82b0798631b9/Pluralsight_-_Blue_Team_Tools_Path.part3.rar.html
NITROFLARE
nitroflare.com/view/826CEC96D9011BE/Pluralsight_-_Blue_Team_Tools_Path.part1.rar
nitroflare.com/view/703ECFB832DEF28/Pluralsight_-_Blue_Team_Tools_Path.part2.rar
nitroflare.com/view/E2613895CF8274B/Pluralsight_-_Blue_Team_Tools_Path.part3.rar